Performance And Security Optimization
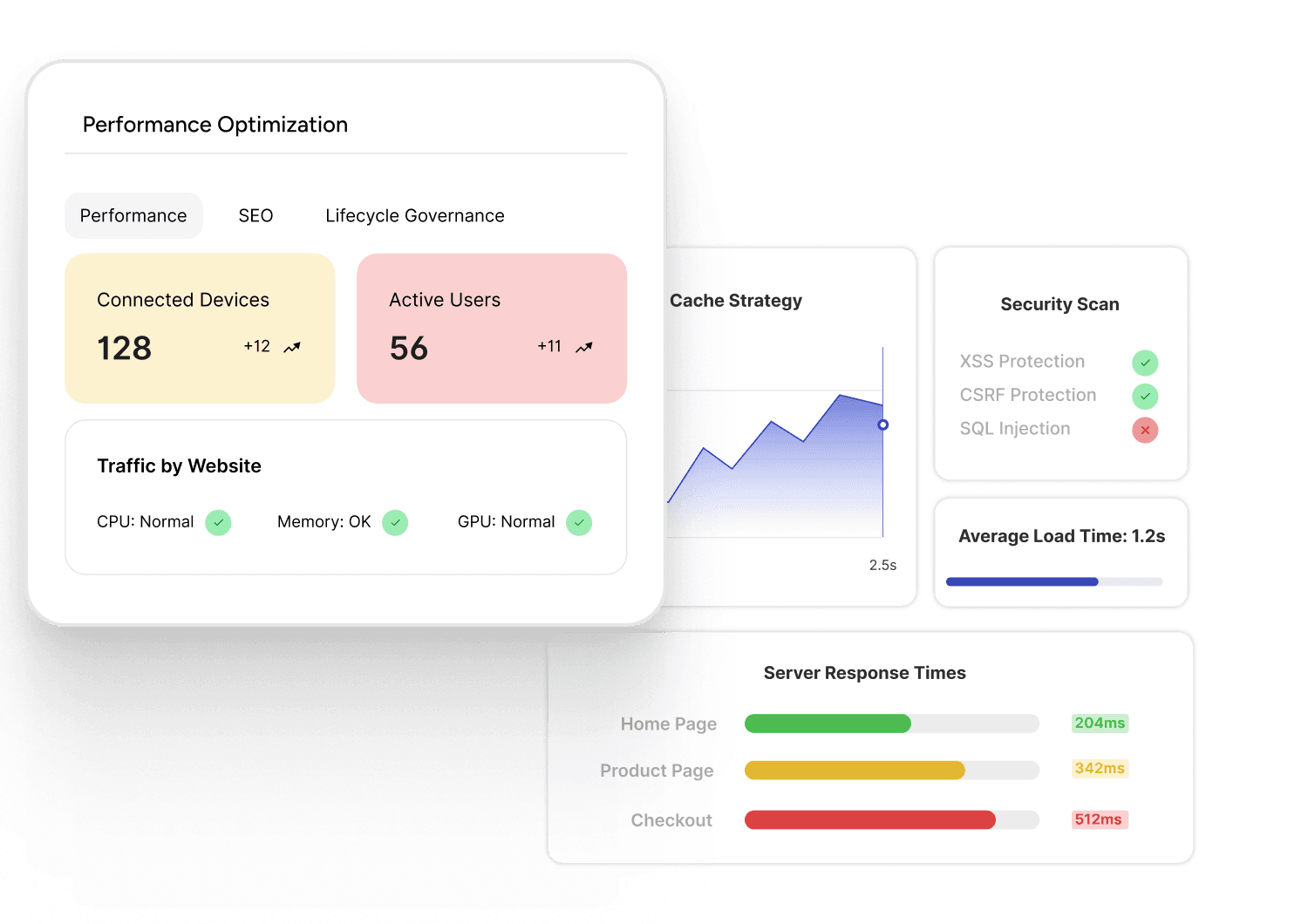
Users expect instant responses and security. Slow applications lose customers, and security breaches destroy trust and create costs.
BUSINESS IMPACT
Why Performance And Security Modernization Matters
Conversion Loss
Data Breach Costs
User Abandonment
Brand Damage
Legal Penalties
Downtime Costs
Measurable Outcomes We Have Delivered
3x
Faster Load Times
Reduce page load times and API response latency.
99.99%
Uptime SLA
Achieve enterprise-grade reliability and availability.
100%
Compliance
Meet GDPR, HIPAA, and SOC2 requirements.
90%
Threat Prevention
Block security threats before they impact users.
50%
MTTR Reduction
Decrease mean time to recovery with better observability.
80%
Resource Efficiency
Optimize infrastructure utilization and cost.
WHAT WE DELIVER
Our Performance And Security Services
Application Performance Tuning
- Application portfolio analysis
- Infrastructure dependency mapping
- Cost-benefit analysis and TCO calculations
- Risk assessment and mitigation strategies
OpenTelemetry Observability
- Distributed tracing with OpenTelemetry
- Metrics collection and visualization (Prometheus, Grafana)
- Centralized logging (Loki, ELK stack)
- APM (Application Performance Monitoring)
Security Hardening (GDPR, HIPAA)
- Security vulnerability assessments
- Penetration testing and remediation
- GDPR and HIPAA compliance implementation
- Encryption at rest and in transit
High Availability & Disaster Recovery
- Multi-region and multi-zone deployments
- Automated failover and recovery
- Backup and disaster recovery strategies
- Circuit breakers and retry mechanisms
SECURITY FOUNDATIONS
Security Best Practices
OAuth2 / OIDC implementation
Role-based access control (RBAC)
Session security
Multi-factor authentication (MFA)
JWT token management
Input validation and sanitization
Protection against OWASP Top 10
SQL injection prevention
XSS and CSRF protection
Secure API design
Network segmentation
WAF and DDoS protection
Container security scanning
Secrets rotation
Security monitoring & SIEM
ENGINEERING STANDARDS
Performance Optimization Strategies
Frontend
- Code splitting
- Lazy loading
- Image optimization
- Tree shaking
- Service workers
Backend
- N+1 query elimination
- Connection pooling
- Async processing
- Rate limiting
- Batch operations
Database
- Index optimization
- Query tuning
- Materialized views
- Read replicas
- Partitioning
Infrastructure
- Auto-scaling
- Load balancing
- CDN integration
- Caching layers
- Edge computing
TECHNOLOGY STACK
Tools We Use for Performance and Security Modernization

Prometheus

Grafana

Opentelemetry

Datadog

New Relic
Our Enterprise Capabilities
Modernization Pillars
FEATURED CONTENT
Our Latest Insights on Performance And Security Modernization
Cloud ERP Integration with AI Process Automation: Real-Time Decision-Making for US Companies

The Importance of UX in Secure Messaging Apps: Balancing Simplicity & Security

Optimize Your Site's Performance with K6 Load Testing

Unmasking Hidden Bugs with the Power of Fuzz Testing in Software Development
A Beginner's Guide to Front-End Security for Fintech Apps Using ReactJS and React Native

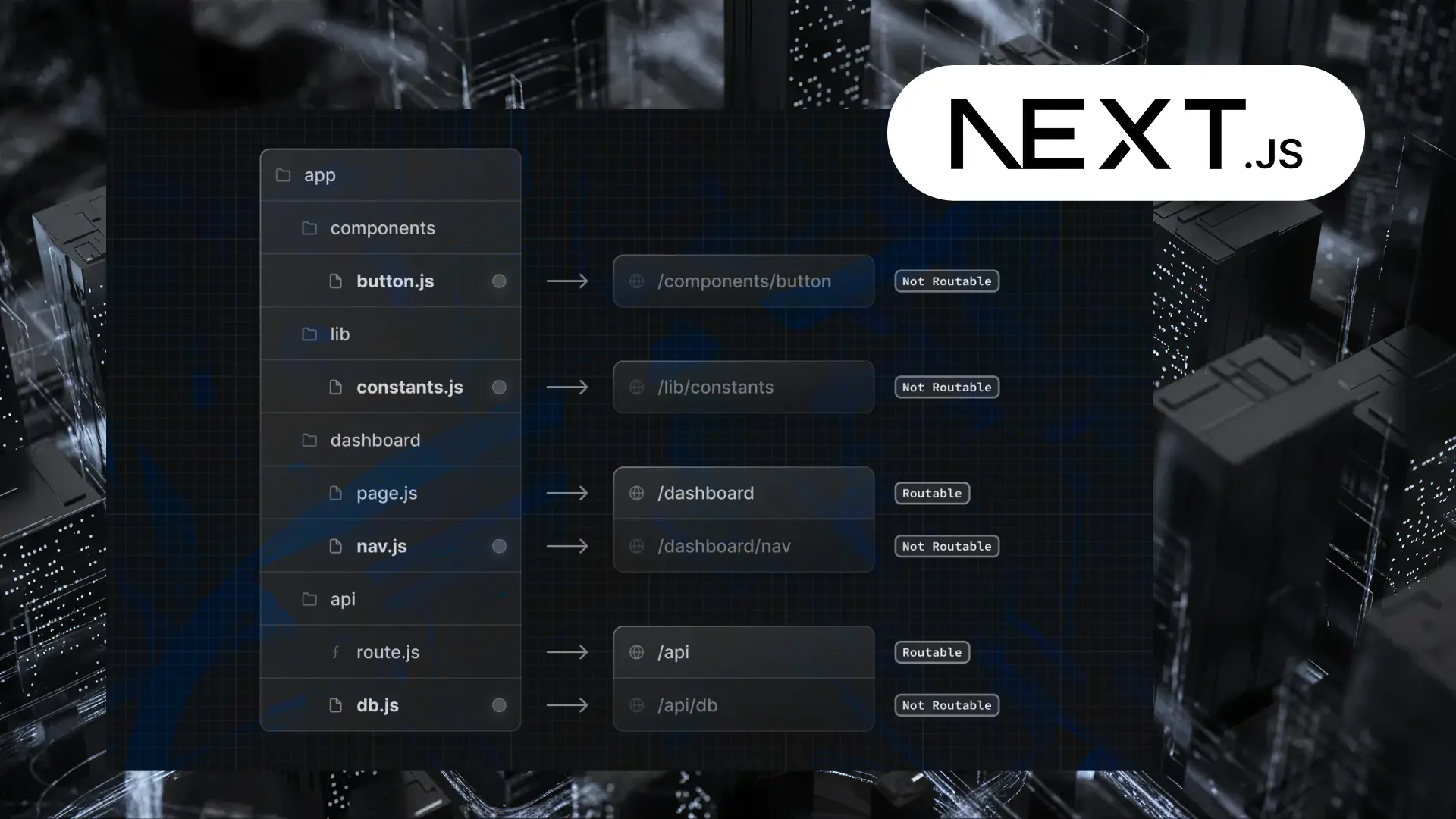
Boosting Performance with Next.js and React Server Components: A geekyants.com Case Study
Scaling your business should not mean compromising on speed and security
Book a call with our performance and security consultants today.
Trusted By
Scaling your business should not mean compromising on speed and security
Trusted By