Table of Contents
Strengthening Spring Security: The Key to Fortifying Your Web Applications
Author
Date

Book a call
Picture Spring Security as the impenetrable fortress guarding your applications against external threats. This customizable package does it all – from authentication and authorization to shielding against notorious exploits like Cross-Site Forgery Requests (CSRF).
Let's start with the fundamentals. Authentication is like the gatekeeper checking your credentials before granting you access to your favorite club. On the contrary, authorization determines what areas of the club you can access once you are inside. It's all about control, ensuring only the right people get into the VIP section of your application.
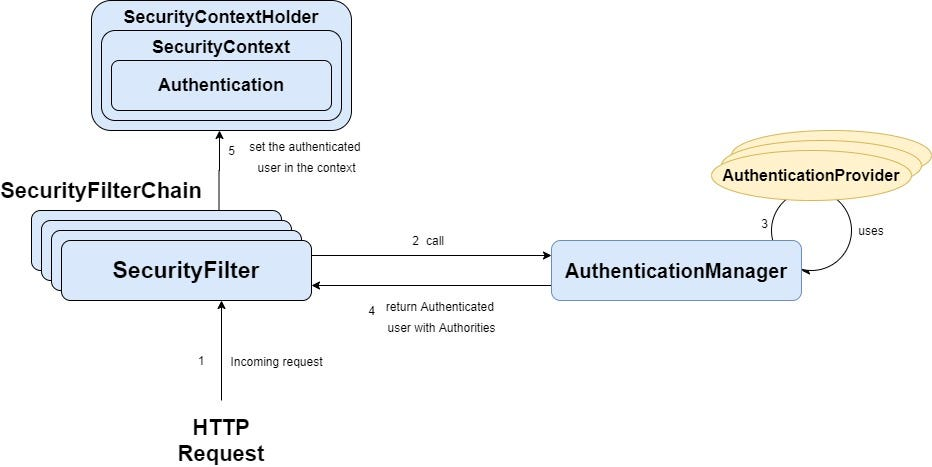
Now, let's dive into the architectural brilliance of Spring Security.
Spring Security swings into action when a request knocks on your backend server's door. If you are using form-based login, users are greeted with a login form, where they enter their username and password.
Here is the play-by-play:
- The user shares their credentials in the request.
- The request journeys through the DelegatingFilterProxy, a set of filters guarding the gates to your backend.
- The DelegatingFilterProxy crafts an authentication request object, packs the provided credentials, and sends it to the Authentication Manager.
- The Authentication Manager takes the stage but can not authenticate the user.
- Enter the Provider Manager! It identifies the appropriate authentication provider based on the authentication type (e.g., username and password).
- The chosen authentication provider fetches user details from the database and scrutinizes the provided credentials.
- If the credentials check out, an authentication response is born and dispatched back to the Provider Manager.
- The Provider Manager relays this response to the DelegatingFilterProxy.
- Voila! The user is now authenticated, but we must stow away this info in the SecurityContextHolder so they can navigate other parts of the application without the hassle of reauthentication.
Spring Security 6: Evolution in Action
Presenting Spring Security 6, with its bag full of improvements:
Say goodbye to duplicated web security configuration adapter classes, as they've been gracefully deprecated.
Embrace the robust Security Filter Chain for configuring security like a pro.
Experience enhanced support for OAuth 2.0 and OpenID Connect.
Navigate the secure waters of reactive applications with confidence.
Migrating to Spring Security 6: A Smooth Transition
If you're contemplating a shift to Spring Security 6, here's your roadmap:
- Ensure you are on Java 8 or higher.
- Consider Spring Boot 2.7 or higher for a smoother experience.
- Swap web security configure adapter classes for the more efficient Security Filter Chains.
- Give a warm welcome to the enable web security annotation.
- Pivot towards expression-based access control, leaving preauthenticated access control behind.
- Embrace the new OAuth2 Client Registration Bean with open arms.
Safeguarding the Future
"Spring Security, a formidable guardian in the realm of secure web applications, elevates the game with Spring Security 6. As developers, we have a duty to keep pace with the latest security innovations and adapt our applications accordingly.”
Watch the full talk here:
Dive deep into our research and insights. In our articles and blogs, we explore topics on design, how it relates to development, and impact of various trends to businesses.


